Firewall Security: The Shareware Method
Broadband Internet technology, with its rapidly increasing availability and affordability, has generated a need to secure personal computers in a way never conceived by its original inventors. Constantly connected PC’s are more prone to malicious attempts by the rising amount of computer hackers and “script kiddies”. To defend ourselves without busting our wallets, several software vendors have stepped up to the plate to offer software-based firewall solutions to protect the average PC user from most attacks prevalent today.
Computers on dedicated connections are more open to Internet-based attacks because they are simply on line more and tend to have a static IP connection, at least for several hours or days at a time. Hackers can use the IP information to form any number of nasty attacks on the systems utilizing those IP addresses. These attacks can be nearly harmless, such as causing a lock up or application crash, or can have serious effects like permanently dropping an Internet connection or damaging the computer system, itself.
A firewall is a piece of hardware or software which monitors, blocks, and routes Internet data through to a computer, while keeping it clean from hack attempts, ping attacks and other kinds of Internet-based trouble. Big business and service providers have been using expensive firewall technology for years, keeping malevolent assaults via the Internet to a minimum. With more and more users connected directly to the Internet via cable modems, DSL connections or even T lines, these solutions have been scaled down to include home users in their market profiles.
For the general Macintosh user, firewall software was much like virus software. When was the last time you even saw a Macintosh virus? For me it was back in 1995, while working for Apple Computer’s Performa technical support line. If there was any place that was going to report a virus, this was it. The virus was non-destructive and simply required eradication with one of the various shareware virus utilities. These days, even such a small invader is unheard of.
MacOSX will soon change that, and firewall technology is no different. The UNIX underpinnings of MacOSX make it more susceptible to attack, both by virus and by malformed or misappropriated Internet packets. Oddly enough, the same thing that makes MacOSX more prone to attacks, also protects it. MacOSX’s updated and revised BSD networking subsystem is far more resilient than traditional MacOS’s and resists attacks with efficiency. Often a user may not even be aware of such attempts.
But protection doesn’t stop with the operating system. Truly protected systems demand additional firewall software. Most of the software available actually takes advantage of the built-in components within MacOSX and extends them, allowing much more flexibility and adding ease of use.
These software-based applications have an advantage over hardware firewalls because of price and availability, as well as flexibility. Hardware solutions can be difficult to install or maintain for the average user. While not for the faint at heart, all the software solutions we used were relatively easy to understand and setup, and most importantly, easy to disable in case trouble occurs. With hardware solutions, disabling the firewall may involve rewiring the network or reconfiguring the hardware via command line or other un-user friendly methods. Of course hardware firewalls, on the other hand, are actually superior to any software solution because they are dedicated to a specific purpose, are always running and do not interfere with other software that may be installed on a system.
For the average home user, the software-based firewall solution is a best buy. Especially because the top two software vendors in this arena offer their software for minimal shareware fees. For this reason, these two are the focus of this article.
The ease in setting up the software is also a benefit. Both applications have a series of windows that ask the user questions to model the solution for each individual network configuration. When completed, the software can be left untouched, providing secure protection from any known Internet attack.
BrickHouse, a shareware solution from Brian R. Hill, is the best shareware firewall solution out there and possibly the best across the board. The install is simple; just drag and drop. Double clicking on the applications starts the process of setting up the firewall, tailored to your network. A setup assistant, accessible at any time, guides the installer through the many security options available.
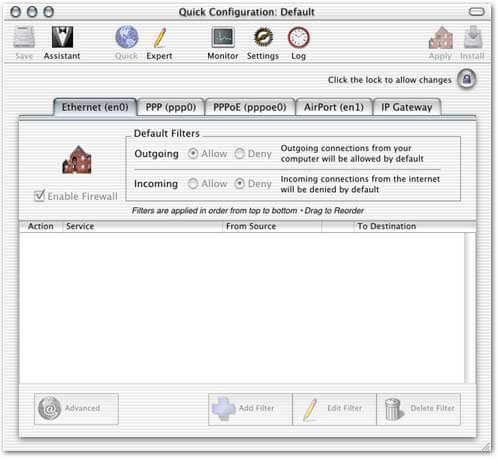
Once all of the options are set a familiar graphical user interface aids the user in additional configurations or modifications to the existing settings. An expert mode allows finite adjustment of the firewall by editing the actual settings files themselves The software also has the ability to share Internet connections with one or more other computers using a single Ethernet card. Monitoring or logging network traffic is also a snap with BrickHouse.
Firewalk is another shareware utility by Mike Vannorsdel that completes relatively the same tasks and even has more in depth questions than BrickHouse, to help customize the level of protection required for the firewall. The GUI is not quite as pretty as BrickHouse’s however, but the application also supports Internet sharing and has many more advanced options to configure the firewall for almost any configuration.
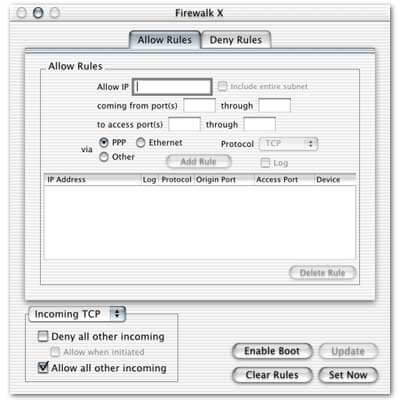
FirewalkX is installed using a custom installer application that places the application itself in the Applications folder, a dockling in the Dock Extras folder and a repair tool also in the Applications folder. The installer will also check for un-prebound software on the drive and optimize its performance. This step make the installation take much longer than BrickHouse’s drag and drop method.
Once installed, options in FirewalkX will be limited if unregistered, allowing only for basic firewall security. While the option for Medium and high security settings are listed in the setup assistant, they are grayed out. The same is true with other options further into the assistant and within the application.
The operation of both firewalls appears seamless. Attacks of a malicious nature are not as prevalent as those who sell this sort of software commercially would have you believe and therefore we can only assume that both were protecting us nicely in this respect. We were unable, however, to penetrate those ports in which we selected to be blocked, which is the fundamental task of both applications
Acting as an NAT gateway, both applications performed markedly better then the manual configuration shown on MacOSX.org’s NAT section. This is possibly due to additional flags used by the applications that were not included in the original manual directions.
While we mentioned that Internet-based attacks of these sorts are less prevalent than originally thought, the simple fact is that they do exist. Protecting a dedicated Internet connection from them should be the goal of any computer user and especially and MacOSX user.
