Connections and Protections
Connections and Protections
Cable and DSL Connections and Security Measures
What type of connection do I have?
Two new remote access technologies are rapidly growing – cable modems and Digital Subscriber Line (DSL) modems/routers. Cable Modems are a shared media. This means that you share a common wire with other people in your neighborhood (see figure one). As more people gain access, the more traffic that is generated over that single wire. Both telco and cable companies are constantly working to increase the amount of bandwidth and service area available to their customers. Unlike their analog cousins, the modem, these media are also always on connections which means as long as your computer is on, it is a node on the internet and susceptible to attacks. Instead of going through a lengthy sign-on procedure, just fire up your favorite TCP/IP application and in a matter of seconds you are online.
Can people see my system?
In this age of always up, shared internet connections to home computers, it behooves one to know as much as possible about being part of a public network. Mac users are lucky in that the Mac OS is a secure system. And while Mac OS 9 has added a Multiple Users option, there is still a strong degree of security. Since you are connected via a shared media, others can see your computer, unless specific steps are taken. This article will help educate you on some protections that can be taken to further secure your system on the internet.
There are ways to protect your system from would be intruders and senseless attacks. It order to see how the systems can be secured, we will first look at what types of attacks are possible, how they affect the system; and then what can be done to protect against such attacks.
While not an attack, another concern is sniffing. Someone connects a sniffer to a network. The sniffer will intercept a copy of every packet that is sent across the network. A sniffer can be set to look a every machine on a given network, or to look at only specific machines. The operator with some time and effort can rebuild the packet and extract the information. This information can be the contents of an e-mail message to an telnet, clear text password.
The best way to beat sniffing is to use encrypted transmissions. Instead of telnet use ssh – secure shell, when using mail use IMAP instead of POP. Both of these clients can’t prevent someone from taking your packets, but they can prevent someone from reassembling them once they have them.
There are some network attacks/integration that even the Mac can’t escape. Two of these are Port Scans and Denial of Service (DoS) attacks.
A Port Scan is when a remote host tries to talk to various network ports available on most machines. Network service, such as the web and FTP, use ports to communicate data. The web usually uses port 80, FTP uses 21 and 20. This allows the attacker to find out what type of OS you are running and also what doorways to your machine are open. If you were running UNIX, there may be a whole host of ports being used and open. A port scan will give an attacker details are to what is up and running on your system.
Denial of Service (DoS) and Distributed Denial of Service (DDoS) attacks are when a remote host floods a specific port with more traffic then it and the system can handle. DDoS utilizes multiple remote hosts all pointing their requests at one machine. The host becomes so busy that it cannot deal with any other requests from remote host or even local hosts. Since it cannot service any other request, it is effectively taken off the network. For example, if you run a web server, a remote host floods your Mac with so many requests that it can’t serve each request. Over a period of time this usually ends up crashing either the application or operating system.
What can be done to thwart attacks and intruders?
There are ways to prevent attacks and intruders. One of the better ways is a tool that Corporations and universities routinely use; firewalls. Firewalls help prevent and log network access. There are two main packages for the Mac OS. NetBarrier and DoorStop. Recently I have looked at both packages. While my home connection is ISDN, I reconfigured my network at home so I installed the security packages on my main machine and tried some tests against them with a PowerBook and Linux box (see figure two). The PowerBook and Linux box represent the Internet in this scenario.
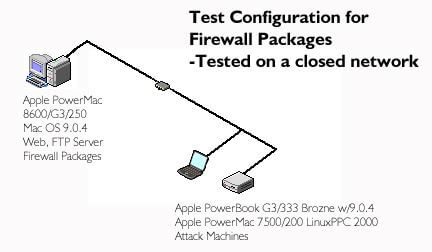
If you are looking for simple setup and functionality, look at the DoorStop package. It is straight forward in both setup and configuration. If you want further control over the configuration of and reporting, try NetBarrier.
Both packages provide basic functionality with the ability to block specific packets from reaching your Mac. NetBarrier seems to have greater control over what can be blocked and the control you have over the application.
Out of the box, the biggest concern with the Mac OS is AppleShare. While a great way to share files with other people, precautions must be taken or you can leave yourself in harms way. Make sure that you don’t have guest access turned on. Instead of guest access, use individual logins. If multiple people need access to an area, setup a group they can use. Check this under the File Sharing Control Panel. Check that all accounts have passwords assigned to them. If any accounts don’t have passwords, either disable the account, or assign a password to it.
If you run any Internet services, such as HTTP (web), FTP, Telnet, mail, etc. on your Mac, you need to take extra care. While these extra services may be necessary for your configuration, they also provide the outside with additional ways in. Many package work to provide security options. Time and testing must be used to secure the services.
Logs can provide a wonderful source of information when looking for signs of attacks. Know what services are keeping logs are review them on a weekly basis. (Also if all looks normal, then you may consider deleting the log. They can grow in size quickly) Look for repeated login attempts from unknown domains, remove all guest accounts. If you use mail, make sure that any relay options are turned off. These systems are used by spammers and blackballed by system administrators worldwide.
Enjoy your high-speed connection. Just be aware of what is possible and the possible consequences. While the chances may be small that it could happen to you, never say never. A little time and education can help greatly in the long run.
Peter N. Hein of Wright State University – Macintosh Software Specialist II. -SecureMac.com
