Mac OS X nidump Security Issues (macosx)
What is nidump?
nidump reads the specified NetInfo domain and dumps a por-
tion of its contents to standard output. When a flat-file
administration file format is specified, nidump provides
output using the syntax of the corresponding flat file.
The allowed values for format are aliases, bootparams,
bootptab, exports, fstab, group, hosts, networks, passwd,
printcap, protocols, rpc, and services.
If the -r option is used, the first argument is inter-
preted as a NetInfo directory path, and its contents are
dumped in a generic NetInfo format.
If the -r option is used, the first argument is inter-
preted as a NetInfo directory path, and its contents are
dumped in a generic NetInfo format.
nidump [ -t ] { -r directory | format } domain
nidump Security Issue in Mac OS X
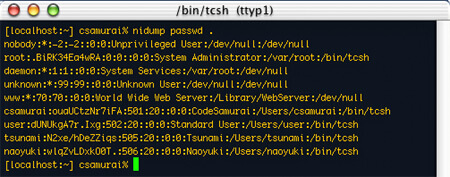
nidump is a Mac OS X data extraction program which defaulty allows readable access to the Mac OS X password file. This was first discussed when the program malevolence was released – malevolence calls commands to dump the content of the passwd file. You may do this job by hand by executing one command:
nidump passwd . or /usr/bin/nidump passwd .
NOTICE:
There is also another readable file which can be read by any text editor to retrieve account information: /var/backups/local.nidump
When a user does this they can use the hash file in a password cracking utility to decrypt the passwords, including root account!
The Fix:
Currently the only fix is to change the permissions and restrict who may use this application. To restrict nidump execute the following command at the command line:
chmod 550 /usr/bin/nidump

