SecurityOn this week’s Checklist, we’ll see how private your iCloud backups really are; we’ll examine the strange story of how the richest person in the world got hacked; and finally, we’ll look at a technology that promises a better way to do 2FA.
This week on the Checklist:
Considering iCloud and end-to-end encryptionA WhatsApp bromance gone badIf you’ve got an iPhone, here’s FIDO!
What happens in your iCloud…
We’ve known for a while that iCloud backup data isn’t protected by end-to-end encryption — meaning that encryption keys aren’t stored only on the user’s device, …
January 23, 2020 •
10 min read
SecurityRather than doing something to protect yourself, we’ll challenge you to teach someone else about cybersecurity and help them take steps to keep themselves safe.
January 22, 2020 •
10 min read
SecurityOn this week’s Checklist, we’ll take a look at someone else’s checklist of security tips, plus we’ll talk about what happens when companies that don’t specialize in security decide to get into the security business.
January 16, 2020 •
10 min read
SecurityBy testing your knowledge of the full spectrum of phishing tactics out there — by seeing what you know…and what you don’t — you’ll be better equipped to deal with even the sneakiest of phishing attempts.
January 14, 2020 •
2 min read
SecurityThe California Consumer Privacy Act (CCPA) is legislation designed to protect the digital privacy and consumer rights of residents of the State of California.
January 13, 2020 •
6 min read
SecurityThe U.S. Department of Homeland Security has issued an alert about a “critical vulnerability” affecting Mozilla’s Firefox browser. The DHS has advised all Firefox users to update their browser software immediately.
In this short article, we’ll explain what the vulnerability is, help you parse the language used in the security advisory, tell you who is affected, and let you know how to get your updates and stay safe.
What is the vulnerability?
According to the Mozilla security advisory, the vulnerability was due to a flaw in the “IonMonkey JIT compiler”, which could “lead …
January 11, 2020 •
6 min read
SecurityIt’s the first Checklist of 2020, and we’re starting things off with some important privacy news from the great state of California. We’ll also discuss (another) potential issue with Amazon’s Ring doorbell surveillance camera. And finally, we’ll leave you with a decidedly low-tech security tip that you’ll want to remember all year long!
January 9, 2020 •
8 min read
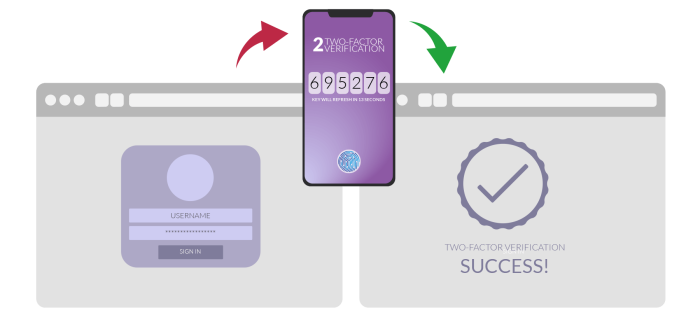
SecurityTwo-factor authentication, or 2FA, is one of the best cybersecurity tools available to you. The main benefit of two-factor authentication is that it adds another layer of protection to your accounts and services, above and beyond passwords
January 8, 2020 •
11 min read
SecurityAndroid has started rolling out Rich Communication Services (RCS) chat features to users of its Messages app, touting this as a better, more up-to-date successor to traditional SMS texting. However, there is still some confusion about what RCS is…
January 7, 2020 •
6 min read
SecurityMany people are aware that large tech companies like Facebook and Google collect and monetize user data . But privacy advocates are now sounding the alarm about the growing trend of consumer banks and credit card companies doing the same thing.
January 6, 2020 •
8 min read
SecurityThis January, we’re going to offer you the chance to make some changes which will improve your cybersecurity posture and keep you safer all year long. To do this, we’ll give you some background information on each “cybersecurity New Year’s resolution” and also walk you through the steps needed to take action.
For many people, these may be things that they’ve been putting off for a while — things that they know are important, but which they haven’t gotten around to just yet. If that describes you, now’s the perfect time …
January 2, 2020 •
8 min read
SecurityThe Checklist is taking a little holiday break this week, but we’ll be back on the 9th of January with a new podcast. Until then, we’d like to invite you to check out these classic Checklists you might have missed, especially as they touch on topics that have been in the news of late!
In what follows, we’ll let you know what’s been going on in the world of cybersecurity for the past week, and then we’ll point you to a Checklist where you can learn more.
This Best of the Checklist …
January 2, 2020 •
5 min read